Secure by design.
Scaled with ease.
Consolidate your sites, reduce attack surface, and eliminate constant patching with a platform built for security from the ground up.

Secure by design.
Scaled with ease.
Consolidate your sites, reduce attack surface, and eliminate constant patching with a platform built for security from the ground up.
Trusted by over 300,000 of the world’s leading organizations
Webflow empowers every creator to build securely on an enterprise-grade foundation to move fast, use AI responsibly and stay compliant.
Compliance at a glance
Webflow maintains third-party certifications that validate how we handle data, access, and operational controls across our platform.
SOC 2
Demonstrates continuous compliance and operational rigor across core systems.
ISO 27001
Validates that Webflow applies structured, organization-wide security controls.
ISO 27017
Confirms best practices for securing cloud environments and shared responsibilities.
ISO 27018
Ensures data handling aligns with global privacy expectations and safeguards.

PCI-DSS
Covers how Webflow meets the security requirements for handling and transmitting payment information.
Security built into every layer of the platform
From infrastructure and network protections to access controls and governance, Webflow gives teams the autonomy to move fast with the guardrails engineering and security expect. Branching, staging, approvals, and version visibility keep changes contained, while Site Activity Log and API-level versioning make it easy to see who made what change and roll it back if needed.
Reduce risk by reducing the surface area
Security without the maintenance load
Webflow removes the weekly patch cycles and plugin hardening most platforms require. No customer-managed updates, no dependency drift, and far fewer vulnerabilities to track.
Consolidate sites and reduce risk
Multiple CMS instances, plugins, and hosting setups create blind spots. Webflow centralizes design, CMS, hosting, analytics, personalization, and localization so security teams have fewer systems to secure and monitor.
Lower inherent risk
By reducing dependence on plugins and restricting execution paths, Webflow minimizes the vectors where vulnerabilities typically appear. This leads to dramatically fewer issues to triage and a more predictable security posture.
Related articles
Webflow maintains third-party certifications that validate how we handle data, access, and operational controls across our platform.
Frequently asked questions
Enterprise customers can configure custom security headers including Content Security Policy (CSP), X-Frame-Options, and other critical security headers to add an extra layer of protection against cross-site scripting attacks, iframe embedding, and domain-level security threats. Webflow supports a comprehensive range of security headers that you can enable and customize through your site settings, giving you granular control over your site's security posture.
Webflow includes built-in DDoS (Distributed Denial of Service) protection for all hosted sites, safeguarding your website from malicious traffic attacks that could otherwise take your site offline. This protection operates automatically at the infrastructure level, detecting and mitigating attacks before they can impact your site's performance or availability.
The DDoS protection works seamlessly with Webflow's global content delivery network and hosting infrastructure, ensuring your site remains accessible to legitimate visitors even during attack attempts. This means you don't need to configure additional security services or worry about traffic-based attacks disrupting your business operations.
Yes, Webflow provides automatic SSL certificates and HTTPS encryption for all hosted sites, ensuring secure connections between your website and visitors without any setup required. Every Webflow site benefits from end-to-end SSL security, automatic certificate renewal, and optimized certificates for maximum browser compatibility, protecting your visitors' data and improving your site's search engine rankings.
For additional security control, Webflow automatically enables HSTS (HTTP Strict Transport Security) on all non-Enterprise sites, while Enterprise customers can configure HSTS settings according to their specific security requirements. This comprehensive approach to encryption and security headers ensures your site maintains the highest security standards, protecting both your content and your visitors' information from potential threats.
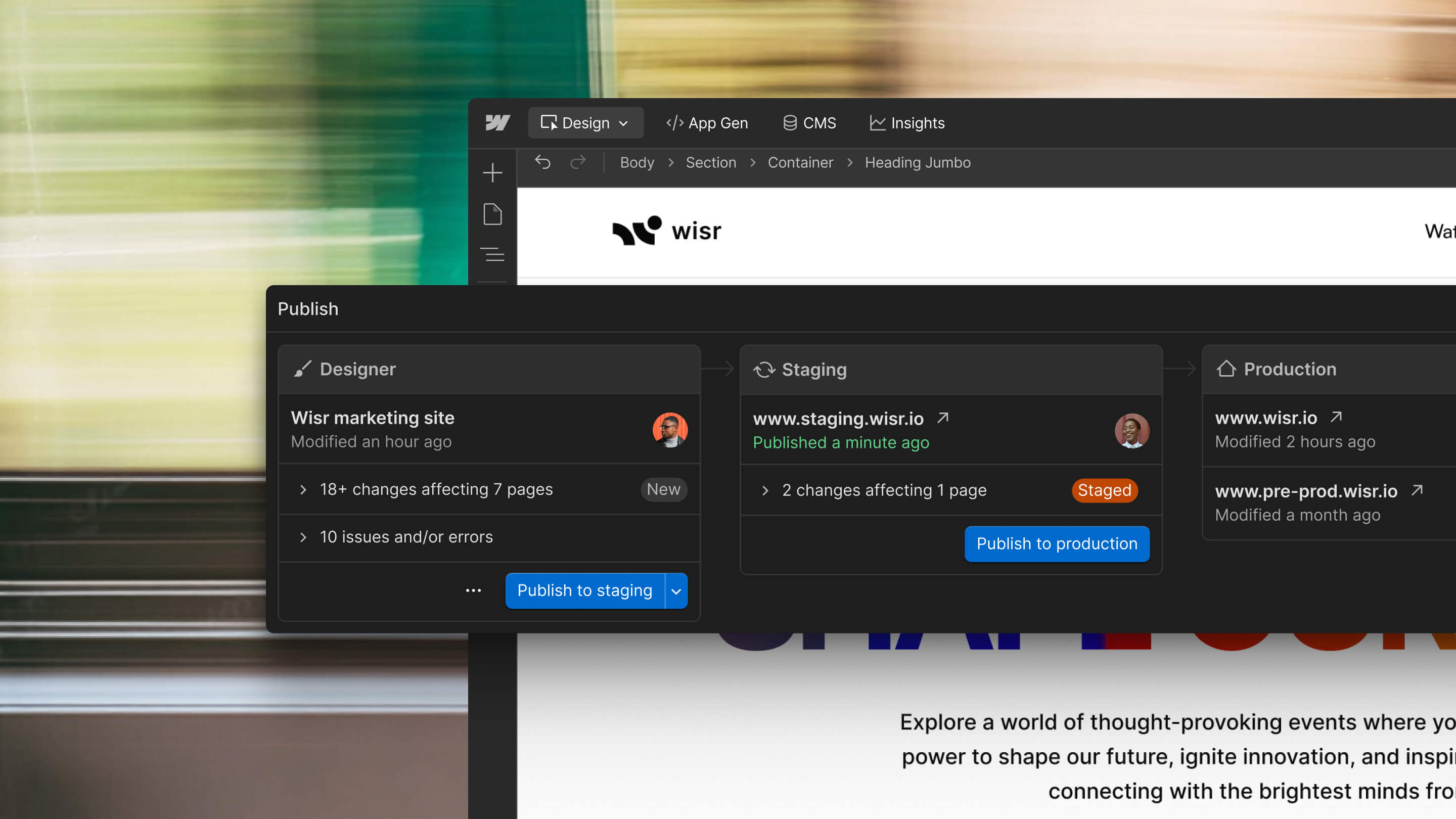
Webflow includes built-in staging capabilities, allowing teams to preview and test changes before they reach production. The platform supports controlled publishing workflows where team members with appropriate permissions can review work before it goes live, ensuring quality control at every step. This staging environment mirrors your production site exactly, giving you confidence that what you see in preview is what visitors will experience.
For organizations requiring more sophisticated approval processes, Webflow's permission system allows you to designate who can publish changes and when. This creates natural checkpoints in your workflow where stakeholders can review, provide feedback, and approve updates before they impact your live site, maintaining both creative freedom and operational control.
Webflow automatically maintains a complete history of all changes made to your site, allowing you to see who made specific modifications and when they occurred. If an issue arises, you can instantly restore any previous version of your site with a single click, eliminating the stress of irreversible mistakes. This comprehensive backup system runs continuously in the background, capturing every edit without requiring manual intervention.
The platform's version control extends beyond simple undo functionality, providing detailed activity logs that help teams understand exactly what changed between versions. This transparency makes troubleshooting straightforward and ensures accountability across your team, giving you the confidence to experiment and iterate knowing you can always return to a stable state.
Webflow provides multiple layers of protection that allow teams to work confidently without compromising site stability. The platform includes staging environments where changes can be tested before going live, comprehensive version control that tracks every modification, and granular permissions that ensure only authorized team members can publish to production. This means designers can iterate freely while developers maintain control over what reaches your live site.
By separating design experimentation from production deployment, Webflow eliminates the traditional tension between speed and safety. Teams can collaborate in real-time, preview changes instantly, and roll back any issues without affecting site visitors, ensuring your business maintains a professional web presence while continuously improving your digital experience.
Webflow provides managed security that removes many risks common in self-hosted or open-source platforms, where teams are responsible for server hardening, plugin updates, and patch management. Webflow handles security updates, SSL certificates, and infrastructure protection at the platform level, reducing operational overhead without sacrificing control.
Compared to other website builders and CMS platforms, Webflow pairs this managed approach with SOC 2 Type II compliance and ISO 27001 certification, along with features like custom security headers and granular access controls. This combination helps teams reduce attack surface and maintenance work while meeting enterprise security and compliance requirements.
Webflow has established a formal Vulnerability Disclosure Program (VDP). If you’ve identified a potential vulnerability, please follow these steps, please Review the program policy to understand If what’s in scope and then Submit your report through our Bug Bounty portal.
Webflow is not HIPAA compliant by default and is not designed to store or process protected health information. Most marketing and informational sites built on Webflow don’t handle sensitive data, keeping them outside HIPAA scope. For regulated use cases, Webflow can be used alongside custom hosting or compliant backends.
Webflow provides comprehensive security measures to protect your websites and data, including SSL certificates for all hosted sites, DDoS protection, and regular security updates managed by our team. Your sites benefit from enterprise-grade infrastructure with automatic security patches, encrypted data transmission, and secure hosting environments without requiring you to manage server security yourself.
Beyond infrastructure security, Webflow offers features like two-factor authentication, single sign-on for Enterprise customers, and granular access controls to protect your account. This multi-layered approach means you can focus on building exceptional websites while Webflow handles the complex security requirements that keep your sites and visitor data safe.
Yes. Webflow maintains SOC 2 Type II compliance, which verifies that our security, availability, and confidentiality controls operate effectively over time.
Webflow is also ISO 27001 certified, an internationally recognized standard for information security management systems. Together, these certifications confirm that Webflow’s security controls are independently audited and consistently applied to protect customer data.