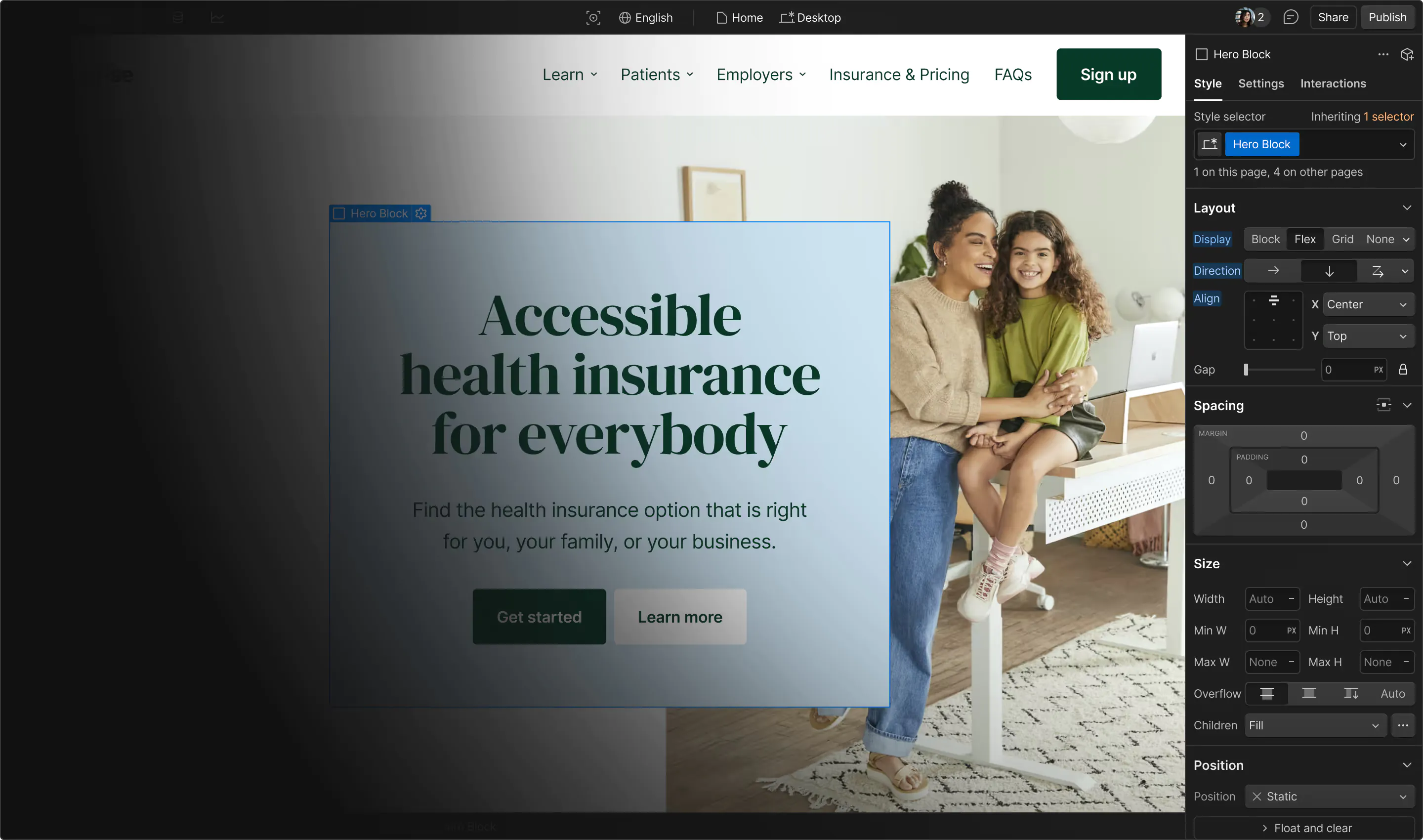
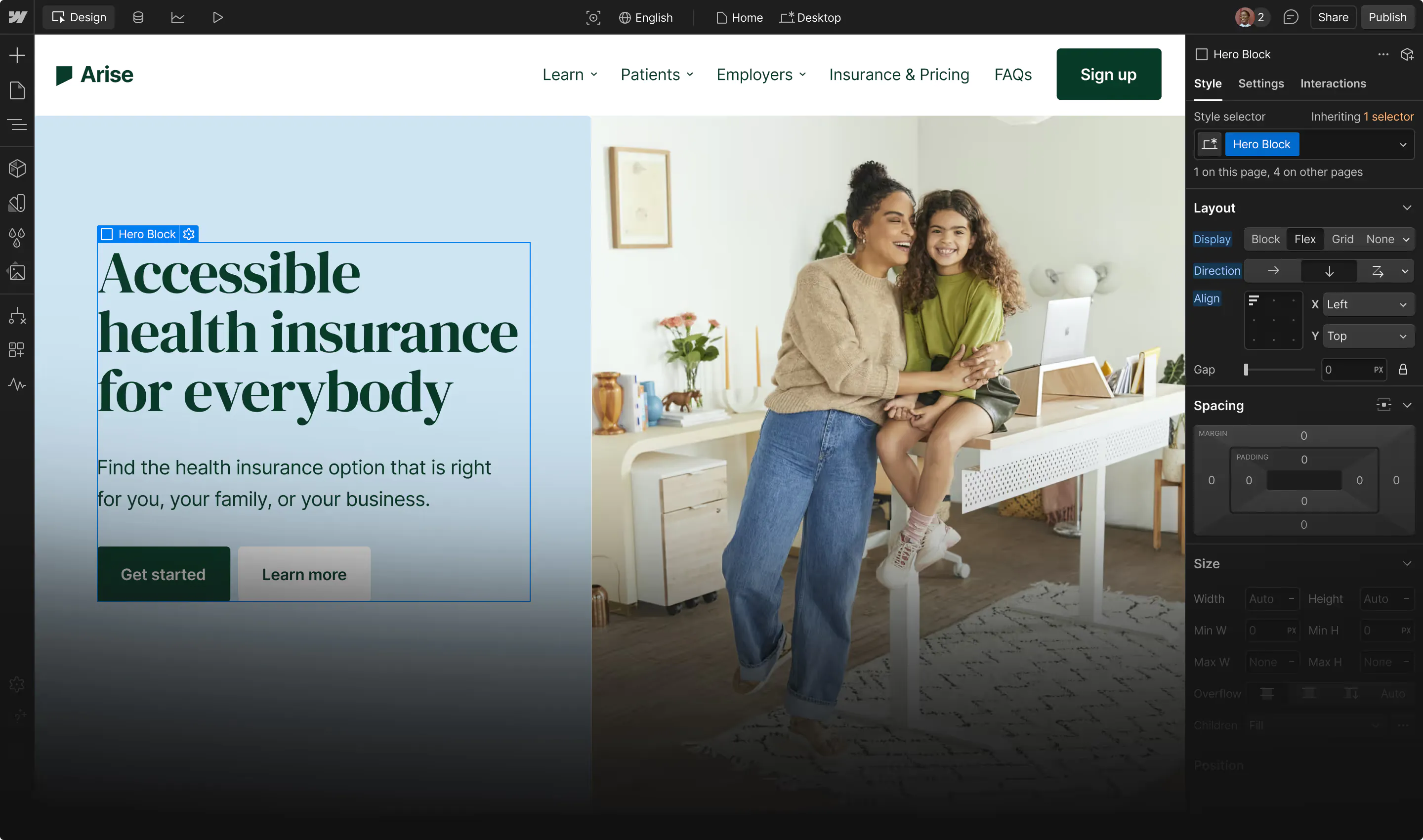
Fortify your website’s defenses with robust user authentication practices.
From confidential customer information to proprietary company data, there’s a lot to protect on a website. Yet, many organizations still rely on outdated user authentication methods, like usernames and passwords, leaving them vulnerable to cyber threats and regulatory review.
Modern-day authentication methods offer multi-layered defense through biometrics, time-based verification, and behavior-based protocols. Read on to learn how this authentication benefits everyone involved.
What’s user authentication for websites?
User authentication involves verifying the identity of people trying to access your website. The system checks credentials against existing records to confirm the user’s identity.
The most common method is username and password-based. Here’s how this process typically goes:
1. User input: Site visitors input their username or email address and corresponding password.
2. Verification: The website compares the username or email address against stored database records.
3. Hashing and comparison: The website uses cryptographic techniques to hash the password, converting it into an encrypted string of characters and comparing it to the password stored in the database.
4. Access granted or denied: If the passwords match, the website grants the user access. If not, the person must try again.
Other common types of user authentication
Username and password-based measures aren’t always the safest. Here are a few modern practices that boost site security:
- Biometric authentication: This involves using unique biological traits (like fingerprints, facial features, and iris patterns) to confirm a user's identity. For example, most smartphones have in-display fingerprint scanners where you place your registered fingerprint in a designated area to unlock the phone. And many Apple devices have Face ID, a proprietary feature that uses the device’s front-facing camera and machine learning to grant access to an iPhone or iPad.
- Two-factor authentication (2FA): With 2FA, users trying to gain entry to your website or application must provide two separate authentication factors for access, such as a password and a one-time password (OTP) sent to their mobile device.
- Multi-factor authentication (MFA): MFA requires users to provide multiple authentication factors, like a password, biometric data, and a reCAPTCHA form.
Crucial components for building safer user authentication methods
Combining these elements for identity verification offers a multifaceted — and safer — approach to site security:
- Knowledge factors: This includes offering information only the user knows, such as passwords, PINs, and security questions. This might involve entering a unique password or answering a question like, "What’s your mother's maiden name?" when logging into an email account.
- Possession factors: This refers to tangible objects — typically a physical token or an internet-enabled device, like a smartphone, tablet, or laptop. The platform sends the user to their device for verification with a password or biometric data to confirm they also own this other device.
- Inherence factors: These are characteristics inherent to the user, primarily for biometric authentication. Users authenticate themselves by providing a unique biological feature that's challenging (and ideally impossible) to replicate, like a fingerprint or facial or voice recognition.
- Time factors: These are time-sensitive authentication methods. Codes that expire after a limited time sent via SMS and email are the most common examples. If someone enters the temporary code after it expires, they can't access the platform.
- Location factors: This method verifies users based on their location. Websites and servers can use HTTP or HTTPS to track locations through IP addresses, GPS coordinates, or cellphone towers and grant or deny access based on a location relative to predefined factors.
The importance of implementing robust user authentication methods
Implementing powerful site security measures offers website owners and users peace of mind. Here’s why prioritizing cybersecurity matters:
- Increased security: Likely the most apparent benefit, verifying user identities through authentication prevents unauthorized parties from accessing sensitive data (like financial, legal, or healthcare information). It also reduces the risk of data breaches and cyber-attacks, which is especially important for enterprise-level organizations with large customer-related datasets.
- Regulatory compliance: Regulations like General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) protect essential data privacy rights. Robust authentication methods protect users and promote safer online experiences.
- Improved accountability: Implementing multi-step authentication showcases your organization’s overall approach to and respect for cybersecurity. It also expresses that you understand that you’re responsible for protecting site users’ data.
- Protection against identity theft: Effective authentication mechanisms prevent fraudulent website access by asking users to provide verifiable, encrypted credentials. Whether that includes passwords or biometric data, having multiple authentication layers in place protects users' against malicious impersonation attempts.
- Positive brand reputation: Showcasing your care for data privacy builds trust and confidence with site visitors. Yes, they’ll feel like their data is in good hands. But this also boosts your overall brand reputation, making happy customers feel inclined to bring more business to your user-focused organization.



















Rethink your CMS
Find out why a cutting-edge enterprise CMS is not just a nice-to-have, but a necessity for teams.
4 best practices for improving user authentication
No matter the access points or datasets you’re protecting, here are four best practices for increasing security through user authentication.
1. Implement multi-layer authentication
Multi-layer authentication methods, like 2FA and MFA, require users to verify their identities using several factors, adding extra layers of security beyond traditional password authentication.
For example, a financial services company can use MFA on their app by asking users to enter a unique password followed by a fingerprint scan and an OTP sent to their mobile device or email address.
2. Enforce strong password policies
Educate visitors about your approach to cybersecurity and user authentication and encourage them to use strong, unique passwords. Offer regular prompts to update outdated passwords and incorporate password manager functionality into your site to help visitors create, save, and manage passwords for quick and safe retrieval. You can even enforce mandatory password requirements, such as minimum length, complexity, and expiration periods.
When signing up for a new account, for instance, your website can ask users to create passwords that are at least 10 characters long and include uppercase and lowercase letters, numbers, and special characters. Then, schedule a popup notification every three months encouraging users to change their password.
3. Monitor user authentication logs
Keep a close eye on authentication logs for suspicious activity, such as multiple failed login attempts or suspicious login locations. Implement automated alerts to notify administrators of potential security breaches and send emails to users to verify whether or not it's really them trying to log in.
For example, your system could notify you of several failed login attempts from different IP addresses within a short period, indicating a potential brute-force attack. This is where hackers use a trial-and-error approach by entering multiple usernames and passwords until they register the correct login details.
4. Use behavior-based authentication
Behavior-based authentication algorithms analyze user patterns to identify anomalies and potential threats. Your site can detect suspicious activities and trigger automated authentication measures by examining factors like typing speed, mouse movements, and navigation actions.
For example, an enterprise website may prompt additional verification if a user suddenly exhibits out-of-the-ordinary behavior, like accessing sensitive data at odd times or from unusual locations.
Secure your website with Webflow
By offering varying levels of security and usability, you can tailor your website's authentication systems based on your resources and the protection level required for your users.
Whether growing a small business or scaling an enterprise, use Webflow Enterprise for increased security measures including reliable traffic management, single sign-on, and advanced DDoS protection. Our platform also leverages Amazon Web Services (AWS) and Fastly to build security directly into your site. Check out our 10-step security checklist and secure your website today.

Webflow Enterprise
Trusted by over 300,000 of the world’s leading brands, Webflow Enterprise empowers your team to visually build, manage, and optimize sophisticated web experiences at scale — all backed by enterprise-grade security.