Protect webhook endpoints from attacks using HMAC signatures, authentication, and monitoring while maintaining performance. Build resilient event-driven systems that stay secure without sacrificing speed.
Webhooks power event-driven architectures from CI/CD pipelines to payment systems, but these HTTP callbacks require exposing permanent endpoints that create security risks.
Read on to learn more about webhook security and eight security measures, including signatures, TLS, authentication, and replay protection. These techniques help technical teams secure webhooks while maintaining performance.
What is webhook security?
Webhooks are HTTP callbacks for real-time communication between services. Unlike polling APIs repeatedly, providers send HTTP POST requests with JSON payloads directly to your endpoint when events occur.
Webhook security protects these callbacks from attacks. Since webhooks receive incoming HTTP requests, attackers can potentially trigger unauthorized actions, steal data, or access internal systems through forged or modified requests.
Unlike polling, where you control outbound requests, webhooks require exposing a public endpoint and trusting incoming requests. This means you need to validate messages, use encryption, and defend against attacks.
Both providers and consumers share security responsibilities. Providers should sign payloads and use HTTPS, while consumers need to verify signatures, authenticate senders, and secure endpoints. Webflow's CMS and App Platform use webhooks for content publishing and form submissions, making these security measures critical for production systems.
Why webhook security matters
Webhooks expose always-on HTTP endpoints accessible to any external service or attacker. When compromised, these endpoints can lead to consequences, including data breaches, service disruptions, unauthorized transactions, and compliance violations, as webhook-triggered workflows often execute automatically without human verification.
Common attacks against webhook endpoints include:
- A Server-Side Request Forgery (SSRF) allows attackers to manipulate callback URLs so your systems make requests to internal resources. This can leak sensitive data when your webhook service trusts user-provided URLs.
- Replay attacks capture legitimate HTTP requests and repeatedly send them to trigger the same action multiple times. For example, an
order.completedwebhook could charge customers repeatedly if replayed. - Traffic interception attacks target webhooks sent over plain HTTP or poorly configured TLS. Attackers can read or modify this traffic before it reaches your application.
- Denial-of-service attacks (DDoS) flood your endpoint with fake requests, overwhelming your system and blocking legitimate events.
Understanding these threats will help you implement the defense strategies outlined in the following section.
8 webhook security best practices
The following practical security measures help protect your webhook endpoints from common attacks while maintaining performance. Each technique addresses a specific vulnerability and can be implemented independently or as part of a comprehensive security strategy.
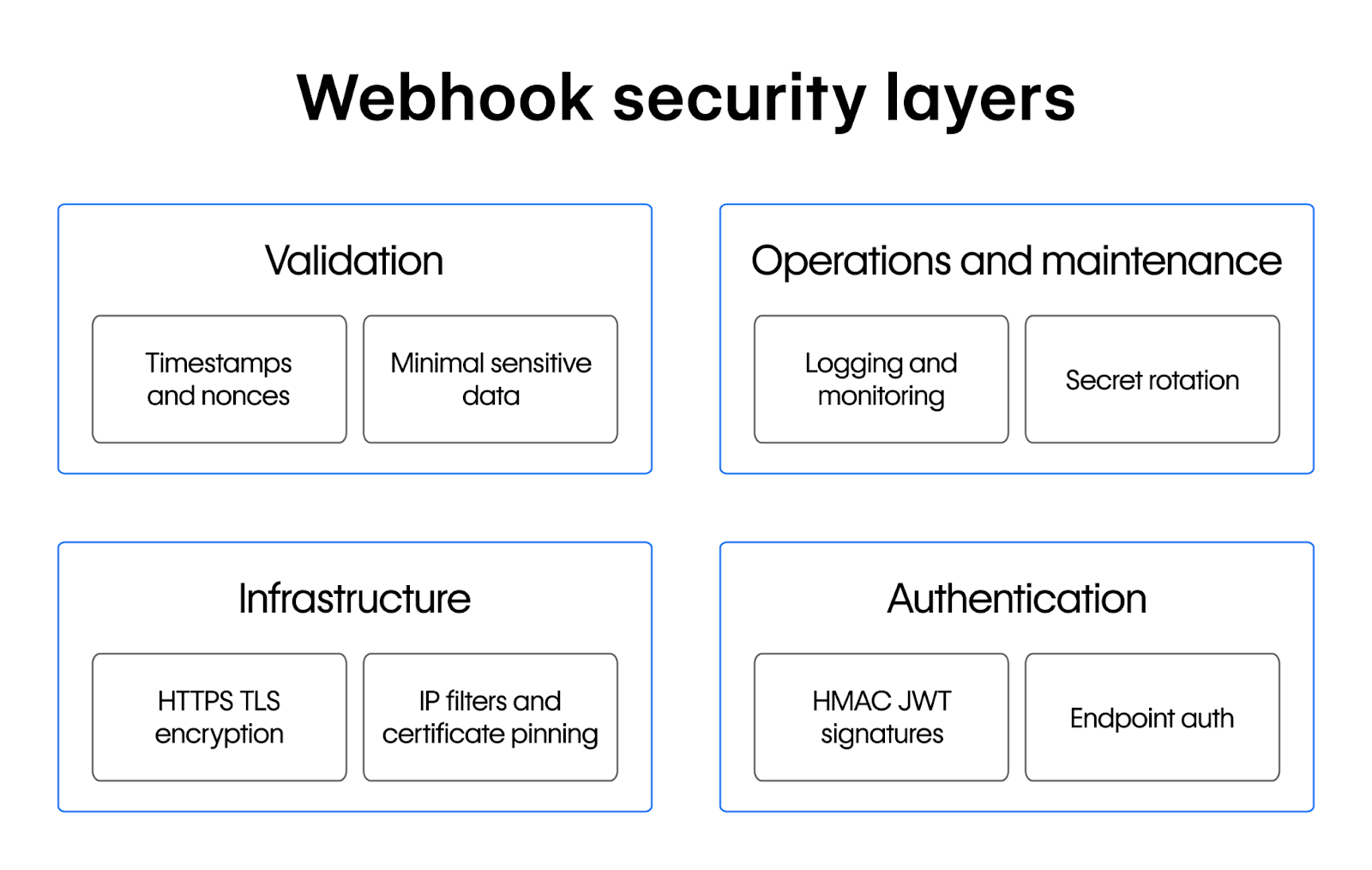
1. Sign every webhook (HMAC or JWT)
Signatures prevent webhook tampering by validating message authenticity and integrity. Most providers, including Webflow, use HMAC, where the provider hashes the payload with a shared secret and sends this hash in a header like X-Signature. You compute the same hash and compare values to detect altered messages.
Most providers use HMAC signatures. Some may issue JWTs for additional context, but this is less common.. It can include context data and supports signing with either shared secrets (HS256) or asymmetric keys (RS256).
// verify-hmac.js
import crypto from 'node:crypto';
export function verifyHmac({ rawBody, header, secret }) {
const expected = crypto
.createHmac('sha256', secret)
.update(rawBody, 'utf8')
.digest('hex');
// constant-time compare to avoid timing attacks
return crypto.timingSafeEqual(
Buffer.from(expected, 'hex'),
Buffer.from(header, 'hex')
);
}
Store secrets in a secure vault rather than source control and rotate them regularly. With proper signature verification in place, forged requests fail before reaching application logic.
2. Always use HTTPS (TLS or mTLS)
HTTPS prevents data exposure by encrypting webhook traffic against eavesdropping and tampering. Plain HTTP transmits payloads in cleartext, making them vulnerable to interception attacks. Standard HTTPS protects traffic through server certificate validation and encryption, which all webhook providers, including Webflow, require.
For higher security, mutual TLS (mTLS) requires certificates from both parties, blocking unauthorized senders before request processing. While effective, it adds certificate management overhead.
Always automate certificate renewal, implement fingerprint pinning where possible, and reject all webhook traffic sent over unencrypted channels.
3. Require authentication for the receiving endpoint
Authentication verifies webhook sender identity to prevent unauthorized access even when HTTPS is used. Common methods include Basic auth with Authorization: Basic base64(user:pass) headers, bearer tokens with Authorization: Bearer <token>, or API keys in headers like X-Api-Key. HMAC signatures also function as authentication.
Always rotate credentials regularly and store them securely outside code.
// express-middleware.js
export function authenticate(req, res, next) {
const token = req.get('Authorization')?.replace('Bearer ', '');
if (token !== process.env.WEBFLOW_WEBHOOK_TOKEN) {
return res.status(401).end();
}
next();
}Layer authentication with signature verification for stronger security. Webflow allows HMAC signature configuration that requires attackers to know your secret to forge requests.
4. Add timestamps (and nonces) to stop replay attacks
Timestamps narrow the replay window, but use nonces or idempotency keys to fully prevent duplicate processing. Adding a UNIX timestamp to your signature lets you reject messages older than a few minutes, which generally blocks replays.
const FIVE_MIN = 5 * 60; // seconds
function isFresh(ts) {
const diff = Math.abs(Date.now() / 1000 - Number(ts));
return diff < FIVE_MIN;
}For stronger protection, implement nonces as unique identifiers stored in a fast database. When a previously seen nonce appears again, drop the request. This approach also provides idempotency during legitimate retry attempts.
5. Use certificate pinning or IP allow-listing
Certificate pinning and IP allow-listing protect webhooks by verifying sender identity at the connection level. Certificate pinning stores expected certificate fingerprints and rejects connections that don't match, blocking attacks even when certificates appear valid. IP allow-listing filters traffic by approved source addresses, providing simpler implementation but less reliability with cloud providers that use dynamic IP ranges.
Where feasible, combine IP allow-listing with certificate validation. Full certificate pinning is difficult at scale and best reserved for controlled environments. Always automate certificate updates and set alerts for validation failures to prevent unexpected downtime.
6. Avoid sending sensitive data in webhooks
Minimize sensitive data in webhook payloads to prevent leaks and reduce security risks. Don't include unnecessary information in webhook messages. Instead of sending personal or payment data directly, use minimal identifiers like this:
/
{
"event": "order.created",
"orderId": "abc123"
}Your backend should fetch complete records through secure API calls with proper authentication. When some sensitive data needs to be included, encrypt it before signing and only decrypt it after verification. This approach simplifies compliance with privacy regulations and limits potential damage from exposure.


















7. Implement robust logging and monitoring
Robust logging and monitoring provide an essential forensic trail for detecting and investigating webhook attacks.
Log only the data you need for security analysis to avoid sensitive information exposure. Store event type, source IP, timestamp, signature validation result, and HTTP status codes without raw tokens, secrets, or personally identifiable information (PII).
Implement a centralized logging system with immutability and role-based access controls. Configure alerts for security anomalies like signature failures, request rate spikes, or traffic from unexpected locations. Follow retention policies that match your compliance requirements and remove outdated logs automatically.
This comprehensive monitoring enables your team to quickly detect attack patterns and strengthen defenses before significant damage occurs.
8. Use subscription models with expiration & rotation
Subscription models with expiration dates minimize risk by preventing stale webhook endpoints from becoming security liabilities. Long-lived endpoints are easy targets for attackers, so implement automatic rotation and forced renewal.
When a client registers a webhook, give them a unique secret with a 30-day expiration and include the expiry in your response. Require clients to renew before expiration and authenticate again during renewal. Generate a new secret and invalidate the old one during this process. Automatically disable endpoints that fail to renew or consistently return error responses.
// pseudo-code for rotating a webhook secret
if (Date.now() > subscription.expiresAt) {
const newSecret = crypto.randomBytes(32).toString('hex');
db.update(subscription.id, { secret: newSecret, expiresAt: nextMonth() });
}Webflow's API supports programmatic webhook lifecycle management so you can automate rotation and cleanup in your deployment pipelines. This approach continuously reduces your attack surface as secrets change and inactive endpoints disappear, making stolen webhook URLs quickly become worthless.
Building a resilient webhook architecture
Building a resilient webhook architecture ensures your security measures remain effective even during attacks by combining defensive controls with fault-tolerant delivery patterns. This approach keeps events processing reliably during traffic spikes or outages.
Start with network-level protection. Webflow Cloud provides global SSL and DDoS filtering at the edge. Add circuit breakers that detect high latency or errors and shed excess load to prevent system failure.
Create a validation gateway that checks HMAC signatures and timestamps before processing. Send verified payloads to a message queue to separate receiving from processing. This approach allows retries and horizontal scaling without data loss.
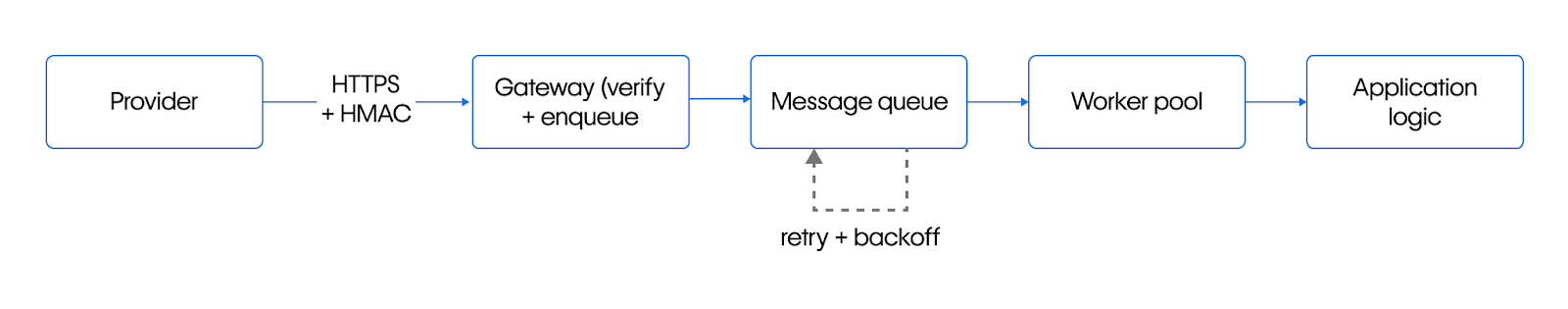
Implement exponential backoff in workers by starting with short delays and doubling them on each retry. Use idempotency keys to prevent duplicate processing of the same event.
Set up monitoring for key metrics like source IP, event type, and validation results. Configure alerts for unusual patterns so you can react before users notice problems.
This combination of edge protection, validation, queuing, and monitoring creates a webhook system that remains operational even during attack attempts.
Key takeaways for developers
Start by implementing the fundamentals:
- Sign every payload with HMAC and reject anything that fails verification. A shared-secret signature prevents spoofing and tampering with minimal overhead, making it one of the most effective controls you can add today.
- Never accept traffic over plain HTTP. Transport encryption with TLS prevents man-in-the-middle attacks and keeps payloads private. Mutual TLS can add two-way authentication when compliance requires it, but standard HTTPS is required for all public endpoints.
- Treat observability as a security feature. Log metadata such as event type, source IP, and signature validation result, but exclude secrets or sensitive fields. Continuous monitoring of failed validations or unusual request rates helps surface replay attempts and DDoS probes before they escalate.
Webhook security is a lifecycle, not a task you finish. Rotate secrets, renew certificates, and review logs on a schedule; automation beats one-off hardening in the long run.
Webflow recommends implementing controls such as enforced HTTPS, strong authentication, and observability for secure and reliable integrations between their composable CMS or App Platform and external services, but these are not officially required for all production traffic.
Explore Webflow's developer documentation to configure signatures, enforce HTTPS, and plug callback events into your existing observability stack. For deeper dives, the resources above provide code-level examples you can adapt immediately.
Webhook security frequently asked questions
How often should secrets be rotated?
Treat a shared secret like a password. Change it on a predictable schedule, at least every 90 days, and immediately after any suspected leak. Most providers, including Webflow, let you generate a new secret and keep both active during a short transition so incoming requests can be verified until all senders update their configuration.
What's the difference between signatures and API authentication?
A signature (typically HMAC) validates the payload. You recompute the hash with your copy of the secret and reject the request if it doesn't match. API authentication using API keys, OAuth tokens, or basic auth controls who can call your endpoint at all.
In other words, authentication keeps strangers out, while a signature proves the message wasn't tampered with and really came from the provider.
Can you use callbacks for sensitive operations like payment processing?
Yes, but limit the data they carry. Webhook callbacks work best as notifications, like "payment succeeded," "refund issued," while the sensitive card details stay inside a PCI-compliant API flow. Sending only identifiers or tokens instead of raw PII reduces risk and still lets you reconcile transactions in real time.
How do you troubleshoot delivery failures securely?
Log metadata like event type, timestamp, source IP, and signature validation result while redacting or hashing headers that contain secrets. Monitor for repeated failures, spikes in traffic, or signature mismatches, then replay events from a safe job queue rather than resending manually. Couple these logs with alerts so you respond quickly without exposing private data.
Do all these security measures hurt performance?
HMAC verification adds negligible overhead compared to network latency. TLS and mTLS introduce milliseconds of extra handshake time, but in practice, these costs are minimal. In practice, network latency dwarfs cryptographic overhead, so you gain strong protection with negligible impact, especially once you queue incoming callback requests and process them asynchronously, as Webflow's recommended architecture does.

Build websites that get results.
Build visually, publish instantly, and scale safely and quickly — without writing a line of code. All with Webflow's website experience platform.